If you need to send an important email, Gmail is the only reliable email sender on this planet. It’s not just Google’s technology that’s reliable; other email services automatically accept mail from Gmail. Any other email service, whether paid or free, might have issues when sending your important emails. Don’t believe me? Here are some personal examples.
Last night, I sent an important email to several business partners using Tutanota. Unfortunately, the email wasn’t delivered and was bounced back. Here’s a screenshot of the bounce message. When I switched to Gmail, the email was sent successfully.
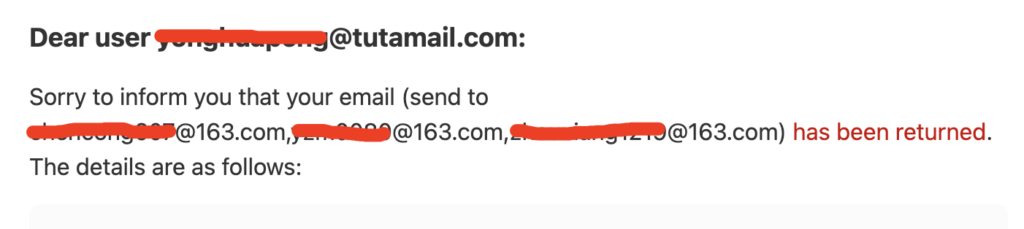
If you use iCloud Mail, sending emails is even less reliable. Your email might be silently discarded. Here’s an example from my experience.
People say Fastmail is great, but Pobox, which is owned by Fastmail, also has sending issues. For instance, one of my emails was rejected because the header contained “php-mailer,” and my account was suspended. Here’s the customer service response.
I reviewed the reason for you receiving this mail and it appears that Vade marked this as spam due to the X-mailer-sender that you used: X-Mailer: PHPMailer 6.5.1The well-known GMX/Web.de also has problems. If you use their email service to send mail from an IP address outside Europe, your message goes through a separate gateway with a spam-listed IP address. As a result, the recipient may not receive your email or it might end up in their spam folder. Here’s a relevant forum post.
Outlook has the same issue as iCloud, with silent filtering, and it might even be worse. Don’t take my word for it; search for online posts about this.
I’m not sure about Yahoo’s current status, as I haven’t used it in a long time. Previously, emails sent from Yahoo servers experienced severe delays, which essentially made the service unreliable.
In conclusion, if you’re sending important emails, just stick with Gmail. Thinking about this, I went ahead and registered dozens of Gmail addresses as backups.